Thanks to rogueamp for making this video.
When running, AVG Antivirus 2011 will display numerous fake security alerts saying "Warning! Active virus detected!" or "Warning! Identity theft attempt detected!". It usually displays such warnings on attempt to run perfectly legitimate programs. For example, it may detect notepad.exe as keylogger or some other malware. This fake AV state that your Windows product key can be stolen.

AVG Antivirus 2011 hijacks web browsers as well and generates fake security warnings. There are mainly two: Internet Explorer Emergency Mode and Attention! Your web page requested has been canceled.
About Internet Explorer Emergency Mode
Your PC is infected with malicious software and browse couldn't be launched
You may use Internet Explorer in Emergency mode - internal service browser of Microsoft Windows system with limited usability.
Notice: Some sites refuse connection with Internet Explorer in Emergency Mode. In such case system warning page will be showed to you.

To sum things up, AVG Antivirus 2011 is a rogue security program that has nothing to do with the legitimate anti-virus program called AVG Anti-virus. It blocks other programs on your computer, hijacks web browsers and displays annoying security alerts about non-existent security threats. It reports false infections and prompts to pay for a full version of the rogue program to remove them. It doesn't have any official website and doesn't provide any contact information. Last, but not least, this fake AVG Antivirus 2011 is promoted through the use of other malware. I think it's obvious that AVG Antivirus 2011 is a scam. If you have already purchased this rogue anti-virus, please contact your credit card company and dispute the charges. To remove AVG Antivirus 2011, please follow the step in the removal guide below. If you have something to add about this threat, please leave a comment. Tell your friends about this infection. Good luck and be safe online!
UPDATE: You can use one of the codes listed below to register the fake AVG Antivirus 2011 (no personal information required). Then scan your computer with anti-malware software.
KNI75-MLM57-CBP65-GPB229-XYL05
NNI90-KOJ66-BCD37-CPA123-XYL21
NDM92-LJD85-IFI74-ODK303-XYL25
AOC55-KBF04-COF00-FAO235-XYL05
DLK35-JNC21-KDF83-CBL035-XYL73
LOD37-GPF25-KKO37-MKM115-XYL44

AVG Antivirus 2011 activation notice:

AVG Antivirus 2011 removal instructions:
Download recommended anti-malware software (STOPzilla) to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
If you can't download it, please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Open Internet Explorer and download STOPzilla. Once finished, go back into Normal Mode and run it. That's It!
Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
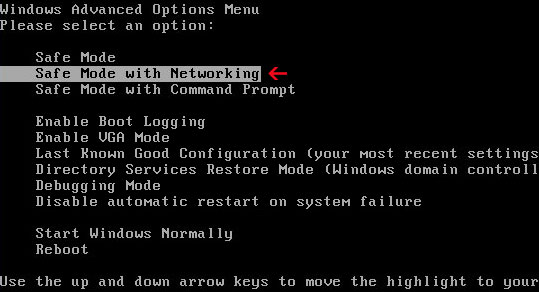
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
AVG Antivirus 2011 removal instructions (Manual):
1. Go into C:\WINDOWS\system32 folder. Locate iesafemode.exe and delete it.

2. Open the Windows Registry Editor. At the taskbar, click Start → Run. Type regedit and click OK or press Enter. (In Windows Vista/7 click the Start button in the lower-left corner of your screen. Type regedit into Start search box and press Enter).

3. Locate the HKEY_LOCAL_MACHINE entry: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iexplore.exe
In the righthand pane select Debugger = iesafemode.exe -sb and delete it if it exists.
Close the registry editor.

4. Open Internet Explorer and download recommended anti-malware software (STOPzilla) to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Associated AVG Antivirus 2011 files and registry values:
Files:
- C:\Documents and Settings\All Users\Start Menu\AVG Antivirus 2011\
- C:\Documents and Settings\All Users\Start Menu\AVG Antivirus 2011\AVG Antivirus 2011.lnk
- C:\Documents and Settings\All Users\Start Menu\AVG Antivirus 2011\Uninstall.lnk
- C:\Program Files\AVG Antivirus 2011\
- C:\Program Files\AVG Antivirus 2011\avg.exe
- C:\WINDOWS\system32\iesafemode.exe
- HKEY_CURRENT_USER\Software\[SET OF RANDOM CHARACTERS]
- HKEY_CURRENT_USER\Software\[SET OF RANDOM CHARACTERS]
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\chrome.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\firefox.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iexplore.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\opera.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safari.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "AVG Antivirus 2011" = 'C:\Program Files\AVG Antivirus 2011\avg.exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\User Agent\Post Platform "WinNT-A8I 28.01.2011"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\chrome.exe "Debugger" = 'iesafemode.exe -sb'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\firefox.exe "Debugger" = 'iesafemode.exe -sb'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iexplore.exe "Debugger" = 'iesafemode.exe -sb'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\opera.exe "Debugger" = 'iesafemode.exe -sb'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safari.exe "Debugger" = 'iesafemode.exe -sb'