Windows XP Repair is a fake system optimization and repair tool that tries to trick users into paying for a version of the program to fix fictitious registry errors and non-existent hard drive problems. It's a rebranded version of
Windows XP Restore and
Windows XP Recovery scareware. And it's also worth mentioning that if you have a computer running Windows XP then the rogue program will install itself as Windows XP Repair. But if you are running Windows Vista or Windows 7 then the rogue program will install itself as Windows Vista Repair or Windows 7 Repair. In other words, this fake application can change its name and graphical user interface depending on the version of Windows that is running.
There are a number of ways that Windows XP Repair gets on your computer, but probably the most common is through fake online virus scanners and infected websites. Usually, fake virus scanners attempt to scare users into downloading fake malware removal tools to remove non-existent viruses. However, it may enter your computer without your knowledge when you visit a compromised website. Drive-by-downloads are very popular and cyber crooks try to use this method of malware distribution as often as they can.
If you suspect or confirm that your computer is infected with Windows XP Repair then you should remove it as soon as possible. To remove Windows XP Repair and related malware from your computer, please follow the steps in the removal guide below. Or you can contact the guys from
KitRx Tech Services Blog to troubleshoot and fix problems caused by this malware. Please note that the following instructions are for users of Windows XP but they should work for those of you who use Windows Vista or Windows 7 too.
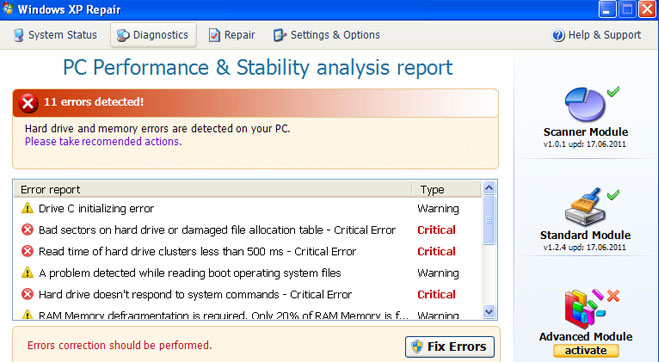
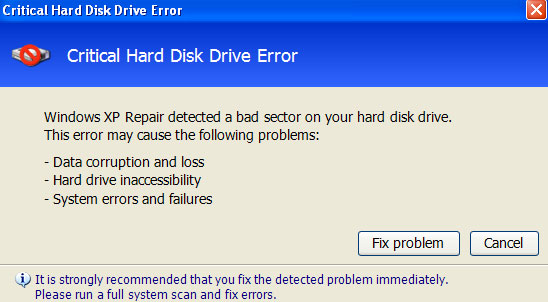
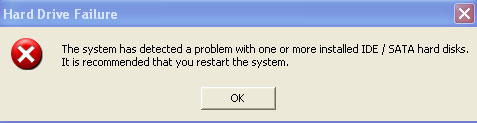
While running, Windows XP Repair will pretend to scan your computer for registry and hard drive errors. It will also display fake error warnings claiming that your RAM memory usage is critically high and that there is a critical hard drive failure which may cause data loss.
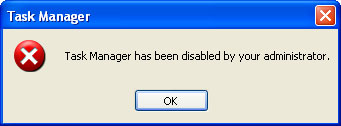
Windows XP Repair will block the Task Manager and hide your desktop icons, certain files and folders to make you think that your computer has some really serious problems. It doesn't delete your files!
You can remove Windows XP Repair manually but honestly this is not something that novice computer users may be able to deal with on their own. Instead of that, you should scan your computer with anti-malware software. Additionally, you can activate the rogue program by entering this registration code 8475082234984902023718742058948 and any email as shown in the image below.
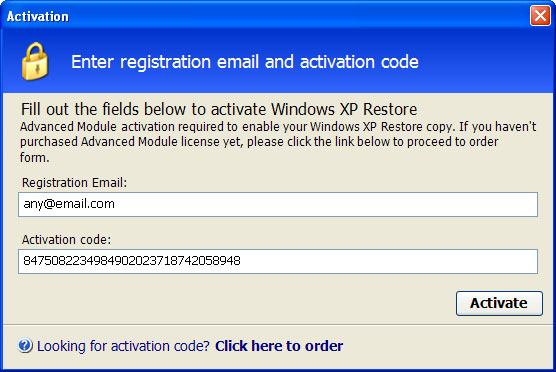
Once this is done, you are free to install anti-malware software and remove the rogue anti-virus program from your computer properly. If you think you have accidentally installed Windows XP Repair, please follow the removal instructions below. And if you have any further questions, please leave a comment below. Good luck and be safe online!
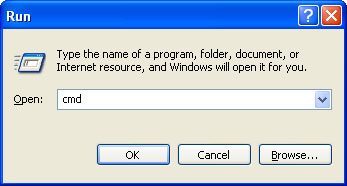
Windows XP Repair removal instructions:1. First of all, you need to unhide the files and folders. Select
Run... from the
Start Menu or just hit the key combination
CTRL+R on your keyboard. In the
Open: field, enter
cmd and hit Enter or click OK.
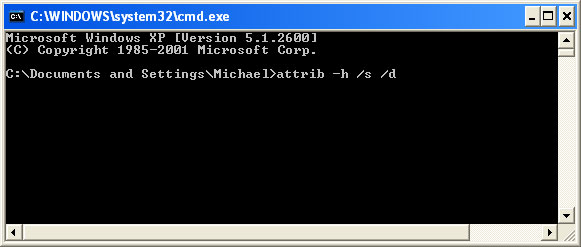
At the command prompt, enter
attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.
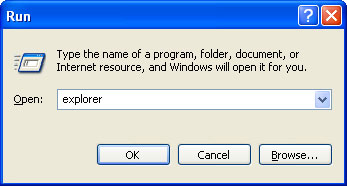
If you still can't see any of your files, Select
Run... from the
Start Menu or just hit the key combination
CTRL+R on your keyboard. In the
Open: field, enter
explorer and hit Enter or click OK.
2. Open Internet Explorer. Select
Run... from the
Start Menu or just hit the key combination
CTRL+R on your keyboard. In the
Open: field, enter
iexplore.exe and hit Enter or click OK.
Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe or
winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Alertane Windows XP Repair removal instructions:1. First of all, you need to unhide the files and folders. Select
Run... from the
Start Menu or just hit the key combination
CTRL+R on your keyboard. In the
Open: field, enter
cmd and hit Enter or click OK.

At the command prompt, enter
attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.

2. The rogue application places an icon or your desktop. Right click on the icon, click
Properties in the drop-down menu, then click the
Shortcut tab.
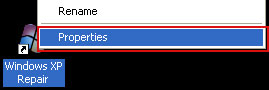
The location of the malware is in the
Target box.
 On computers running Windows XP, malware hides in:
On computers running Windows XP, malware hides in:C:\Documents and Settings\All Users\Application Data\
NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read
Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click
Show hidden files and folders, and remove the checkmark from the checkbox labeled:
- Hide extensions for known file types- Hide protected operating system filesClick OK to save the changes. Now you will be able to see all files and folders in the Application Data directory.
On computers running Windows Vista/7, malware hides in:C:\ProgramData\
3. Look for suspect
".exe" files in the given directories depending on the Windows version you have.
Example Windows XP:C:\Documents and Settings\All Users\Application Data\24436516.exe
C:\Documents and Settings\All Users\Application Data\jTNIGvyiwfxUlB.exe
Example Windows Vista/7:C:\ProgramData\24436516.exe
C:\ProgramData\jTNIGvyiwfxUlB.exe
Basically, there will be a couple of
".exe" file named with a series of numbers or letters.
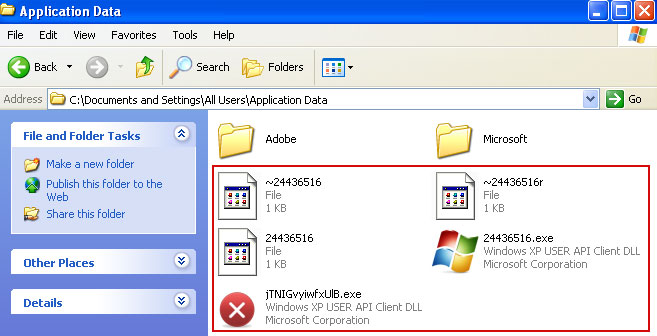
Rename those files to 24436516.vir, jTNIGvyiwfxUlB.vir etc. For example:
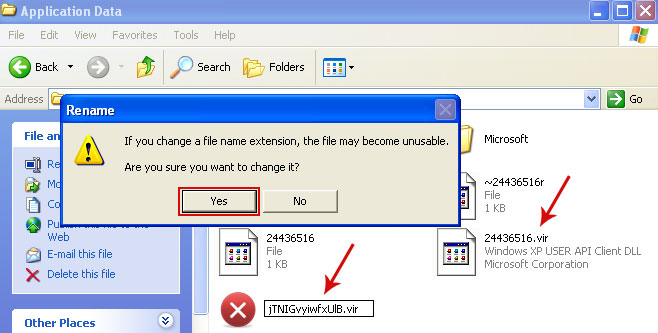
It should be:
C:\Documents and Settings\All Users\Application Data\24436516.virInstead of:
C:\Documents and Settings\All Users\Application Data\24436516.exe4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download
TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.
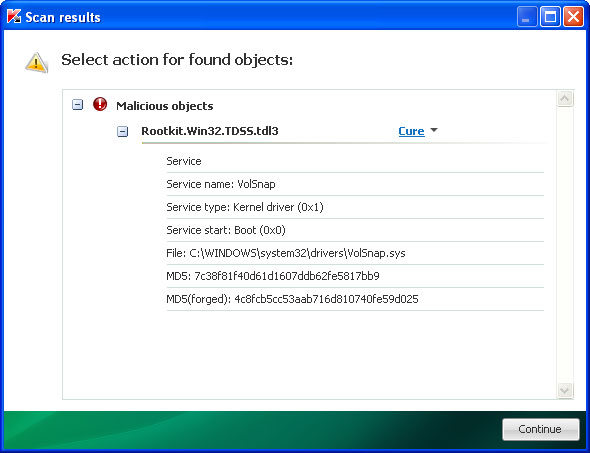
6. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe or
winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
7. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Associated Windows XP Repair files and registry values:Files:
Windows XP:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\Application Data\~[SET OF RANDOM CHARACTERS]
- %UsersProfile%\Local Settings\Application Data\[SET OF RANDOM CHARACTERS].lic
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].dll
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\Windows XP Repair.lnk
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\Windows XP Repair.lnk
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\Uninstall Windows XP Repair.lnk
%AllUsersProfile% refers to: C:\Documents and Settings\All Users
%UserProfile% refers to: C:\Documents and Settings\[User Name]
Windows Vista/7:
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\~[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].lic
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].dll
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\Windows XP Repair.lnk
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\Windows XP Repair.lnk
- %UsersProfile%\Start Menu\Programs\Windows XP Repair\Uninstall Windows XP Repair.lnk
%AllUsersProfile% refers to: C:\ProgramData
%UserProfile% refers to: C:\Users\[User Name]
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'yes'
Share this information with other people:







































