 |
| A screen shot of System Tool malware |
(Thanks to rogueamp)
Usually, this fake program has to be manually installed. But it can be also installed through the use of Trojans without your knowledge and permission. That's why you should keep your anti-virus software up to date and make sure that Windows OS, web browsers, flash player, Java and other software is updated.
System Tool is from the same family as Security Tool scareware. This rogue uses aggressive tactics to trick victims into purchasing the full version of the program. First of all, it displays false system security threats. Furthermore, System Tool blocks any executables that you attempt to run and claims that they are infected. It displays the following error message when you attempt to run any program:
Warning!
Application cannot be executed. The file notepad.exe is infected.
Please activate your antivirus software.


System Tool displays fake security warnings and notifications as well. It will even change your the background of your Windows desktop. Here's how it reads:
Warning!
Your're in Danger!
Your Computer is infected with Spyware!

All you do with your computer is stored forever in your hard disk. When you visit sites, send emails... All your actions are logged. And it is impossible to remove them with standard tools. Your data is still available for forensics, and in some cases
For your boss, your friends, your wife, your children. Every site you or somebody or even something, like spyware, opened in your browsers, with all the images, and all the downloaded and maybe later removed movies or mp3 songs - ARE STILL THERE and could break your life!
Secure yourself right now!
Removal all spyware from your PC!

The rogue program will also claim your private information and PC safety is at risk or that Windows has detected spyware infection. The warning message that you will see is:
Warning: Your computer is infected
Windows has detected spyware infection!
Click this message to install the last update of Windows security software...
Security Monitor: WARNING!The biggest problem is that System Tool terminates all the programs on your computer. You will have to restart your computer in Safe Mode with Networking and scan the system using anti-malware software listed below. Please follow the removal instructions below. It goes without saying that System Tool is nothing more but a scam. If you have already purchased it, the please contact your credit card company and dispute the charges. If you have any questions or additional information about this virus please leave a comment. Good luck and be safe online!
Attention: System detected a potential hazard (TrojanSPM/LX) on your computer that may infect executable files. Your private information and PC safety is at risk. To get rid of unwanted spyware and keep your computer safe you need to update your current security software.
CLick Yes to download official intrusion detection system (IDS software).
UPDATE: you can register System Tool 2011 by using these codes:
(This should make the removal procedure a lot easier)
WNDS-S0DF5-GS5E0-FG14S-2DF8G
WNDS-JUYH3-24GHJ-HGKSH-FKLSD
WNDS-89OF7-7324R-5SAD4-TG68U
WNDS-HFVDR-9844O-U54DA-5TBSC
WNDS-G8FB6-1V87S-DRT1S-63SRG
WNDS-4BGY2-JY4KO-IT98Y-7HJ43
WNDS-5D1V2-XB0D5-JT1TY-97DS3
WNDS-F40SA-1ER5H-4FG5D-F8412
WNDS-SERFH-2642S-F04SD-64FG1
WNDS-S0DF5-GS5E0-FG14S-2DF8G
WNDS-452S3-ER00F-TSE35-S8FSD
WNDS-FGS5D-649RG-4S53D-412SF
WNDS-4TS8R-D6F5D-4JH8T-U4JK5
WNDS-2AE32-1VFC2-B6894-G67YU
WNDS-P9685-4H41A-DSW3A-2R64T
WNDS-5SRTS-AEHUF-YA54S-D6F35
WNDS-A1SDF-RY4E8-7U98D-F1GB2
Thanks to S!Ri for these codes!
System Tool removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
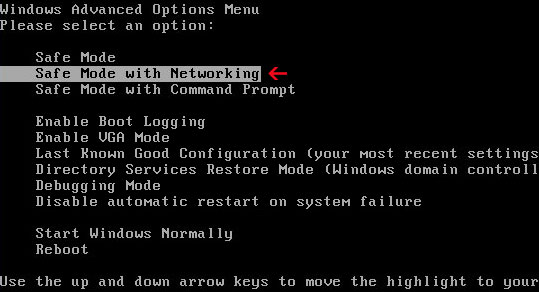
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
Alternate System Tool removal instructions using HijackThis or Process Explorer (in Normal mode):
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download explorer.scr and run it.
2. Search for such entry in the scan results:
O4 - HKCU\..\RunOnce: [dfbLa00902] C:\Documents and Settings\All Users\Application Data\lGAlF00902\lGAlF00902.exe
The process name will be different in your case [SET OF RANDOM CHARACTERS].exe, located in:
C:\Documents and Settings\All Users\Application Data\ in Windows XP
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you may download Process Explorer and end System Tool process:
- [SET OF RANDOM CHARACTERS].exe, i.e. lGAlF00902.exe
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
System Tool associated files and registry values:
Files:
- C:\Documents and Settings\All Users\Application Data\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\All Users\Application Data\[SET OF RANDOM CHARACTERS]\[SET OF RANDOM CHARACTERS].exe
- C:\ProgramData\[SET OF RANDOM CHARACTERS]\[SET OF RANDOM CHARACTERS].exe (Windows Vista, Windows 7)
- KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "[SET OF RANDOM CHARACTERS]"
No comments:
Post a Comment