- Windows was configured to use a proxy.
- Blocks legitimate security products and system tools
- Displays misleading security alerts
- Asks to purchase the program
- Runs on system start-up
- Drops a rootkit
Files:
- %WINDIR%\System32\[SET OF RANDOM CHARACTERS].exe
- %Userprofile%\Application Data\dwm.exe
- %Userprofile%\Application Data\Microsoft\conhost.exe
- %Temp%\csrss.exe
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"
Quick tip: run Windows Configuration Utilities. Type MSCONFIG in the search box and press enter. Select Startup tab and unchecked any program that was just a bunch of characters, usually a bunch of random numbers. Then follow the removal instructions below.
Security Guard 2012 removal instructions:
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
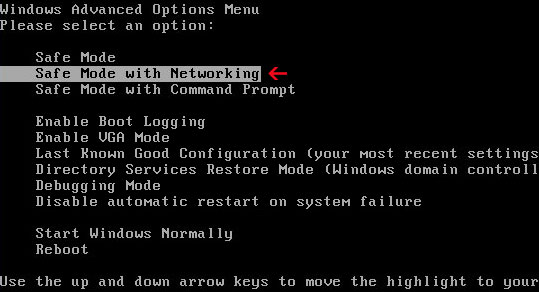
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
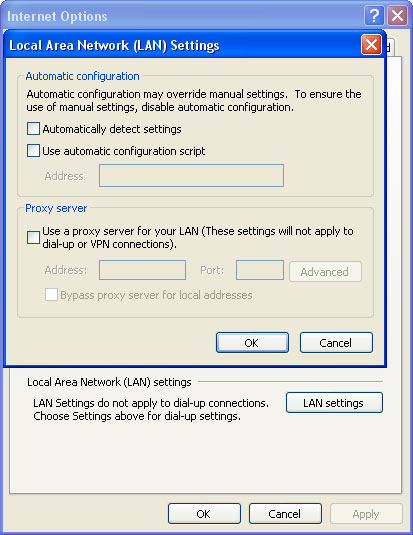
2. Launch Internet Explorer. In Internet Explorer go to: Tools → Internet Options → Connections tab. Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK. You may have to repeat steps 1-2 if you will have problems downloading malware removal programs.
3. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. Go back to Normal Mode and follow the TDSS, Alureon, Tidserv, TDL3 removal instructions to remove the rootkit from your computer.
Share this information with your friends:
No comments:
Post a Comment