POLITIELet op!!!Onwettige activiteiten gedetecteerd!!!Uw operationele systeem is geblokkeerd wegens inbreuk op de de Nederlandse wetgeving!Volgende inbreuken zijn gedetecteerd: Uw IP adres is geregistreerd op de websites met clandestien en/of pornografische content, die pedofilie, zoöfilie en geweld tegen kinderen aanmoedigen! Op uw PC zijn er videobestanden met pornografische inhoud en elementen van geweld en kinderporno ontdekt!Tevens worden illegale SPAM berichten van terroristische aard van uw PC automatisch overal heen verspreid.Deze blokkering heeft in het oog de verspreiding van deze gegeven van uw PC op het internet tegen te gaan.

As, you can see, you need to pay cash at any retailers linked to Paysafecard and thus receive a secure PIN printed on a card. Once you have the PIN, you need to email it to info@politie-nederland.net and receive unlock code. Basically, paying customer is given a key eliminates the annoying warning. The problem is that unlocked can't be debugged because it's not hard-coded in the malicious code. Usually, such extortion scheme works very well. Of course, you shouldn't pay a dime and remove the POLITIE Onwettige activiteiten gedetecteerd from your computer as soon as possible. You just need to reboot your computer in Safe Mode and delete certain Windows registry value. To remove this ransomware from your computer, please follow the removal instructions below. And don't worry, police won't knock-knock at your front door. Good luck and be safe online!
Related ransomware:
POLITIE, Onwettige activiteiten gedetecteerd!!! ransomware removal instructions:
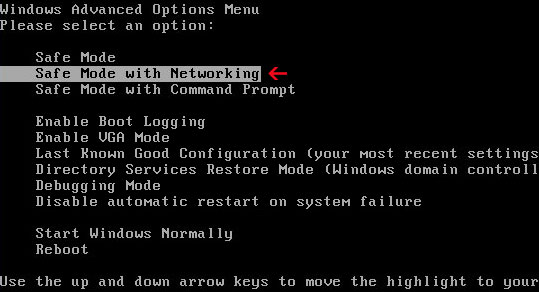
1. Reboot your computer is "Safe Mode". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. When Windows loads, open up Windows Registry Editor.
To do so, please go to Start, type "registry" in the search box, right click the Registry Editor and choose Run as Auto Infoistrator. If you are using Windows XP/2000, go to Start → Run... Type "regedit" and hit enter.
3. In the Registry Editor, click the [+] button to expand the selection. Expand:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run

Look on the list to the right for an item named "vasja". Write down the file location. Then right click "vasja" and select Delete. Please note, that cyber crooks may change file names and registry values, so in your case it might be named different. But it will be located in exactly the same place.
4. Restart your computer into "Normal Mode". Delete the malicious file noted in the previous step.
5. Download recommended anti-malware software and scan your computer for malicious software. There might be leftovers of this infection on your PC.
POLITIE Ransomware removal video:
Maxstar, who runs the pcwebplus.nl website, has created a video showing how to remove POLITIE, Onwettige activiteiten gedetecteerd!!! ransomware.
Write-up: http://www.pcwebplus.nl/phpbb/viewtopic.php?f=222&t=5525
Associated POLITIE, Onwettige activiteiten gedetecteerd!!! malware files and registry values:
Files:
- [SET OF RANDOM CHARACTERS].exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run = "vasja"