
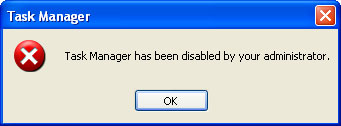
PC Repair is not a typical hijack the Desktop/block task manager type of infection. It really messes up the infected computer. First of all, it hides your files and moves to %Temp%\smtmp folder. DO NOT delete files from your Temp folder. Once you delete those files, you won't be able to recover then unless you have a recovery CD or a back-up image of your entire hard drive. Secondly, this rogue program usually comes bundled or drops a rootkit on the infected computer. It is very important to scan your computer for rootkits before removing the rogue program; otherwise will pop-up again. Most of the time, PC Repair drops a rootkit from the TDSS/Alureon family. That's why we recommend scanning your computer with TDSSKiller. For more, information, please follow the removal instructions below.
Additionally, you can activate the rogue program by entering this registration code 8475082234984902023718742058948 and any email as shown in the image below.

Once this is done, you are free to install anti-malware software and remove the rogue anti-virus program from your computer properly. And remember, do not purchase PC Repair. If you have already bought it, please contact your credit card company and dispute the charges. If you have any questions or need additional help removing PC Repair, please leave a comment below or email us. Good luck and be safe online!
Fake PC Repair warnings:

Related malware:
PC Repair removal instructions:
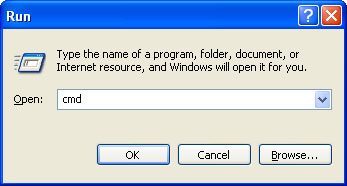
1. First of all, you need to unhide the files and folders. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter cmd and hit Enter or click OK.
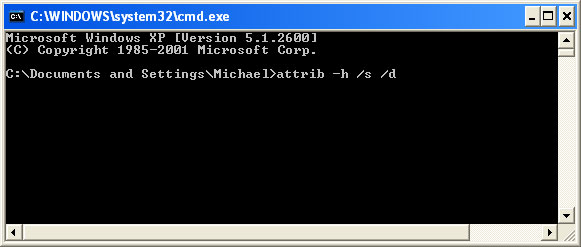
At the command prompt, enter attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.
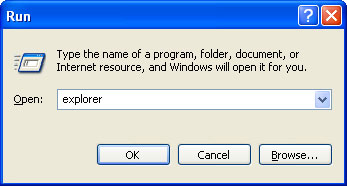
If you still can't see any of your files, Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter explorer and hit Enter or click OK.
2. Open Internet Explorer. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter iexplore.exe and hit Enter or click OK.Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as Auto Infoistrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. Open Internet Explorer and download TDSSKiller or Backdoor.Tidserv Removal Tool. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller or Backdoor.Tidserv Removal Tool to remove the rootkit.
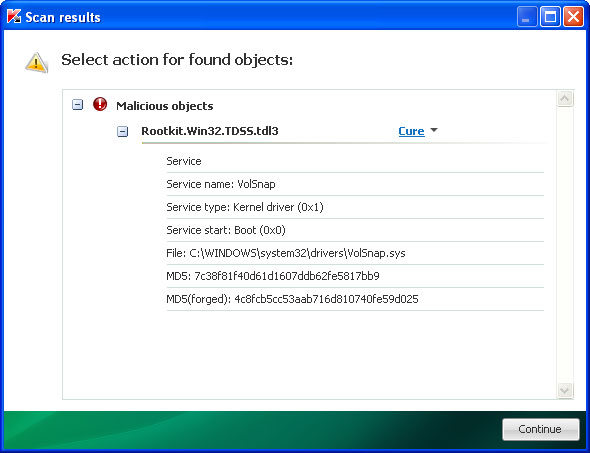
Associated PC Repair files and registry values:
Files:
Windows XP:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\PC Repair.lnk
- %UsersProfile%\Start Menu\ProgramsPC Repair
- %UsersProfile%\Start Menu\Programs\PC Repair\PC Repair.lnk
- %UsersProfile%\Start Menu\Programs\PC Repair\UninstallPC Repair.lnk
%UserProfile% refers to: C:\Documents and Settings\[User Name]
Windows Vista/7:
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\PC Repair.lnk
- %UsersProfile%\Start Menu\Programs\PC Repair\
- %UsersProfile%\Start Menu\Programs\PC Repair\PC Repair.lnk
- %UsersProfile%\Start Menu\Programs\PC Repair\Uninstall PC Repair.lnk
%UserProfile% refers to: C:\Users\[User Name]
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'yes'
No comments:
Post a Comment