
Antimalware Defender is promoted and installed through the use of Trojans that come from fake online anti-malware scanners and similar bogus web sites. Once installed, Trojan virus display fake “System Security Update” window and claims that you AntimalwareDefender is a very important security update. The fake security update reads:
Antimalware security update for Windows XP (KB961118)
Size: 433KB
This critical update will install System Security Update 2010.01.023 (Antimalware Defender Upgrade; KB648759)

I’ve search for an update with code name KB961118 and guess what? Such update doesn’t exist. Once the rogue program is installed, it runs a fake system scan and reports a variety of infections and security issues just to make you think that your computer is infected. Please note, that AntimalwareDefender reports real infections, I mean it uses real names and descriptions of existing threats to make it look more reliable in case someone would search for then on the Internet. The most important thing is to realize that your computer is free of those infections; the only real infection is Antimalware Defender. After the fake scan, this virus claims that you should purchase the program in order to remove the infections and to protect yourself. Well, that’s nothing new. All scamware does that. Just don’t trust it and don’t buy this bogus software.
Antimalware Defender associated files can be found in several different folders. Most of its files are randomly named. The rogue is linked with rundll32.exe process so probably it will block any attempt to remove the malicious files manually unless you end the main process. Also, this scareware adds a Browser Helper Object (BHO) in Internet Explorer. Your search results will likely be hijacked.
Antimalware Defender removal instructions:
1. Download an anti-malware application from the list:
2. Install selected anti-malware application, update it and run a full system scan.
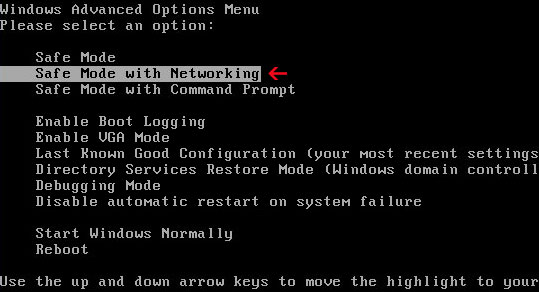
NOTE: the rogue program may block legitimate security software. If you can't install any of the malware removal tools listed above, please reboot your computer is Safe Mode with Networking" and re-download the chosen anti-malware application.
How to reboot your computer is Safe Mode with Networking? As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
Antimalware Defender associated files and registry values:
Files:
- C:\Program Files\Antimalware Defender
- C:\Program Files\Antimalware Defender\Antimalware Defender.dll
- C:\Documents and Settings\All Users\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.avi
- C:\Documents and Settings\All Users\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.ico
- C:\Documents and Settings\All Users\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.mkv
- C:\WINDOWS\system32\ca84c702-c758-4421-974e-b02662e76d7c_6.avi
- C:\WINDOWS\system32\ca84c702-c758-4421-974e-b02662e76d7c_6.ico
- %UserProfile%\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.avi
- %UserProfile%\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.ico
- %UserProfile%\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.mkv
- %UserProfile%\Local Settings\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.avi
- %UserProfile%\Local Settings\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.ico
- %UserProfile%\Local Settings\Application Data\ca84c702-c758-4421-974e-b02662e76d7c_6.mkv
Registry values:
- HKEY_CLASSES_ROOT\CLSID\{ca84c702-c758-4421-974e-b02662e76d7c}
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{ca84c702-c758-4421-974e-b02662e76d7c}
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "ca84c702-c758-4421-974e-b02662e76d7c_6"
If you have any questions, please leave a comment.
Share this information with other people:
No comments:
Post a Comment