
Virus Protector video: (thanks to rogueamp)
You are probably wondering where did it come from? Well, the answer is fairly simple. Most of the time such programs come from fake malware scanners. Virus Protector can be also distributed through the use of fake video websites or using social engineering methods. One way or another, once installed this pesky virus runs fake system scan and reports many fake infections. Furthermore, it displays fake warnings and notifications about serious security problems. Some of the fake alert will state:
"Spyware Alert!
Your computer is infected with spyware. It could damage your critical files or expose your private data on the Internet. Click here to register your copy of Virus Protector and remove spyware threats from your PC."
"Process Blocked!
Harmful memory infection was detected.
Process [name].exe was terminate"
As you can see, Virus Protector has only one goal - to steal money from inexperienced users. Don't be fooled by this rogue program. If you already purchased it, contact your credit card company and dispute the charges. Please read further to find you how to remove Virus Protector from your computer for free. If you have any questions, don't hesitate and ask! Good luck!
Removing Virus Protector in Safe Mode with Networking:
IMPORTANT UPDATE: if this virus disables everything and you can't reboot your PC in Safe Mode or Safe Mode with Networking then try this:
a) Reboot your PC in Safe Mode with Command Prompt.
b) From there type in the following line (below) and hit Enter button:
%systemroot%\system32\restore\rstrui.exe
c) If everything goes well it will restore a system to an earlier date when your PC as not infected.
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
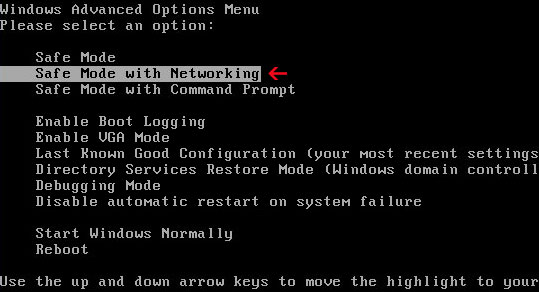
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
If you can't reboot your PC in Safe Mode with Networking, download SafeBootKeyRepair and run it. If the rogue program blocks it then download and run this file RenamedSBKRepair. Follow the prompts. Then reboot your PC in Safe Mode with Networking.
2. Download one of the following legitimate anti-malware applications and run a quick system scan. Don’t forget to update it first. All programs a free.
NOTE1: if you can't run any of the above programs you must rename the installer of selected program before saving it on your PC. For example: if you choose MalwareBytes then you have to rename mbam-setup.exe to iexplore.exe, explorer.exe or any random name like test123.exe before saving it.
NOTE2: if you still can't run the renamed file then you need to change file extension too not only the name.
1. Go to "My Computer".
2. Select "Tools" from menu and click "Folder Options".
3. Select "View" tab and uncheck the checkbox labeled "Hide file extensions for known file types". Click OK.
4. Rename mbam-setup.exe to either test123.com or test123.pif
5. Double-click to run renamed file.
Virus Protector files and registry values:
Files and folder:
- C:\Documents and Settings\[User]\Application Data\[random]
.exe - C:\Documents and Settings\[User]\Application Data\[random].dll
- C:\Documents and Settings\[User]\Local Settings\Temp\[random].exe
- C:\Documents and Settings\[User]\Local Settings\Temp\[random].dll
- C:\Program Files\Internet Explorer\[random].exe
- C:\Program Files\Internet Explorer\[random].dll
- C:\WINDOWS\system32\[random].exe
- C:\WINDOWS\system32\[random].dll
- C:\WINDOWS\system32\drivers\[random].exe
- C:\WINDOWS\system32\drivers\[random].dll
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Virus Protector"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows "LoadAppInit_DLLs" = "1"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows "AppInit_DLLs" = "[random].dll"
Share this information with other people:
No comments:
Post a Comment